NTLMv2 and Kerberos
Introduction
Authentication within a Windows domain relies on the NTLM or Kerberos protocols. NTLMv2 is deprecated, but it is still used as a backup when Kerberos fails.
Note: Active Directory is a solution developed by Microsoft for the management of an information system. It contains:
- a resource directory service (LDAP)
- an authentication scheme (Kerberos)
- a domain resolution service (DNS)
- a software policy
In this example, let’s consider the user Alice who tries to authenticate! We detail the authentication scheme for:
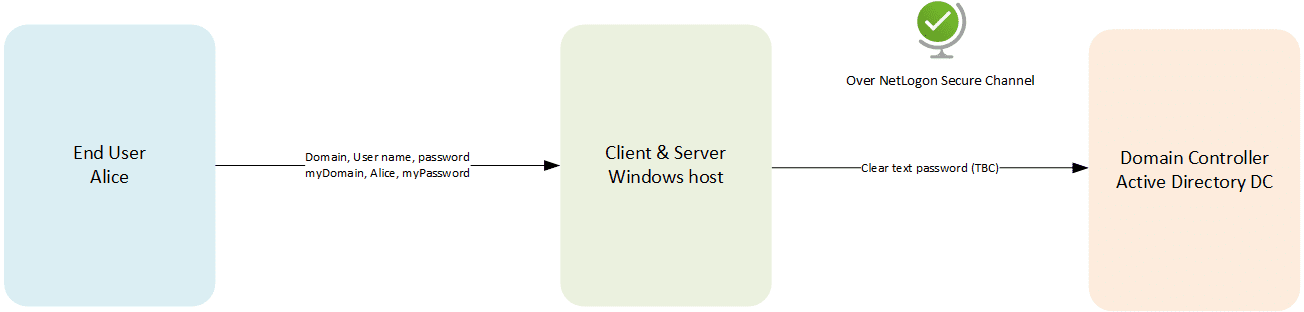
- interactive logon: the user provides inputs for authentication against a server or a Domain Controller.
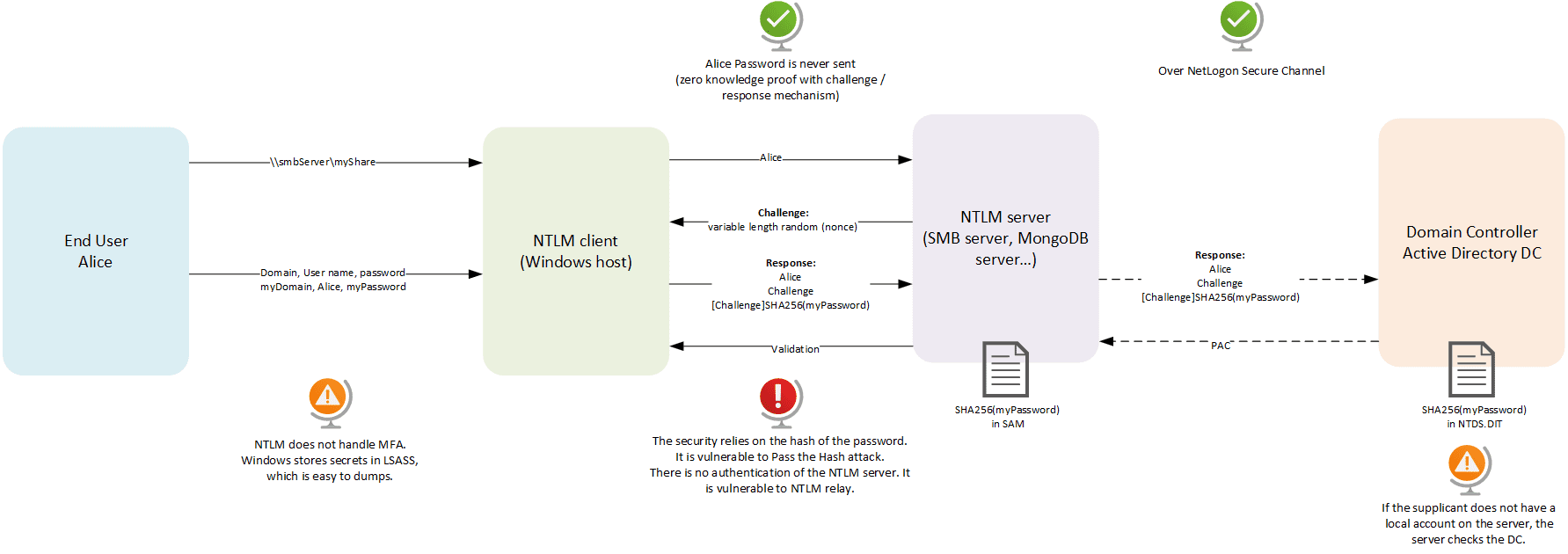
- network logon: the authentication performed by the user as part of interactive logon is used again to log the user on another resource.
Interactive logon with NTLM
Network logon with NTLM
Kerberos
Kerberos is the successor of NTLM. And guess what? It is also broken! ![]() Let’s review the Kerberos authentication process, and illustrate the most common attacks on Kerberos.
Let’s review the Kerberos authentication process, and illustrate the most common attacks on Kerberos.
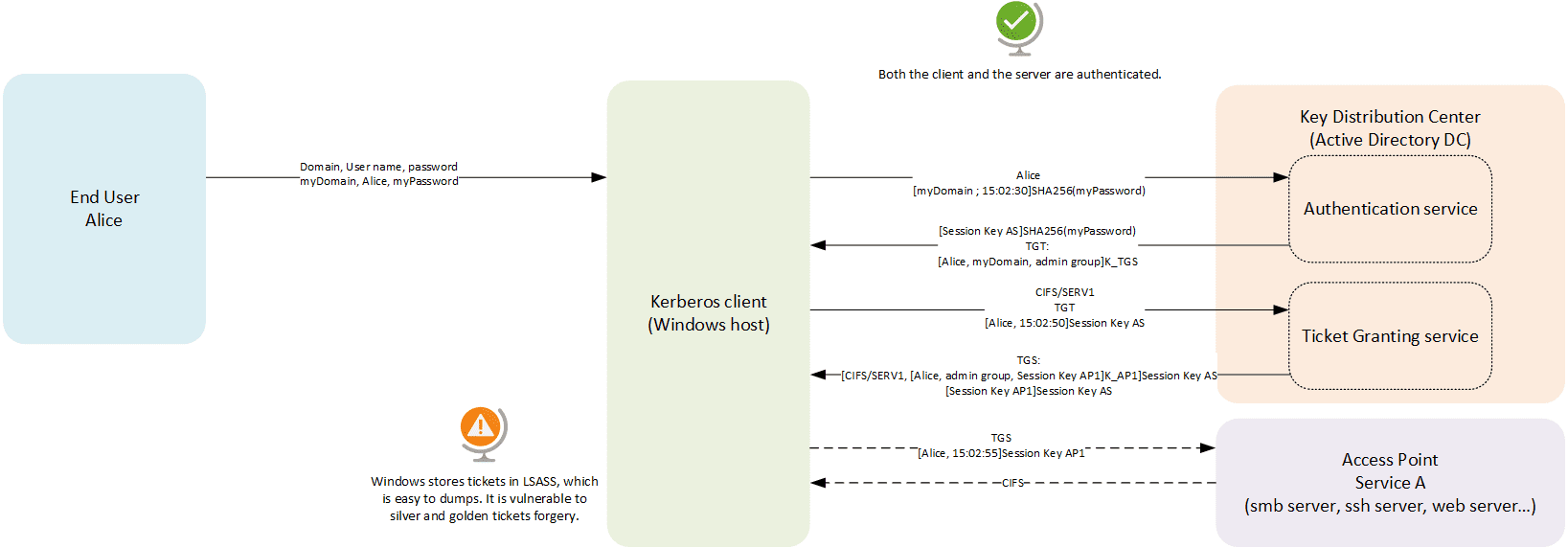
Note: Based on original learning material from Microsoft engineers.