Authentication schemes
Introduction
All the authentication schemes rely on one of 3 authentication means:
- shared secret: the user proves its identity by disclosing its password (a shared secret). Depending on the authentication scheme, the user authenticates by disclosing a password or passphrase (basic authentication), the hash of a password (digest authentication or NTLM), an API key, or a token for a web app… It can be permanent or temporary (nonce).
- symmetric cryptography: the user proves its identity by performing a cryptographic operation based on a shared secret (a symmetric key). Based on the authentication scheme, the user generates a keyed-hash message authentication code (HMAC), or the output of a symmetric-key algorithm (AES). The message can be complemented with additional information (JWS bearer with HMAC is just a string with more information). The symmetric key may even directly derivate from a password with a Key Derivation Function (KDF).
- asymmetric cryptography: the user proves its identity by performing a cryptographic operation based on a private secret and a disclosed value (a public / private key). Based on the authentication scheme, it can be the output of an asymmetric-key algorithm (RSA or ECDSA), and can be complemented by a digital certificate (TLS).
Note: A lot of authentication schemes (protocols) exist for authentication. Some of them rely on direct transmission of the secret, while others use a challenge – response pattern. An authentication scheme may allow for several authentication means. For example, Kerberos may work with both symmetric or asymmetric cryptography. Depending on the protocol, the authentication may be performed at a different OSI layer (application layer for basic authentication, transport layer for TLS, datalink layer for Radius 802.1X).
Type 1: « What I know » 
Something that I can remember. While it is by far the most common type of authentication, it is also considered as the weakest (weak passwords, reused on several applications…). Common examples include:
- Password or passphrase
- API Key
- Personal Identification Number (PIN)
- Personal Unblocking Key (PUK)
- Security questions
- Pattern
Type 2: « What I have » 
A lot of different technologies already exist:
- TOTP (Time-Based OTP): nonce incremented every 30 seconds (Google Authenticator)
- HOTP (Hash-based OTP): nonce incremented on each pressure
- POTP (Push notification OTP): nonce not even disclosed to the user generated on approval These OTP can be received by SMS or phone call (SIM card ownership). They can also be generated by an authentication application (software token), or by a physical device (hardware token). Some other authenticators not relying on an OTP exist:
- Chip card: private key securely stored in a physical device, non exportable
- Passport or other official documentation.
Authentication devices may use different protocols for exchanging information (bluetooth, NFC, USB…).
Type 3: « Who I am » 
A biometric parameter: a shared measurement (the position of points on a fingerprint or a face, the modulation of a voice, even the DNA!…). It is considered more secure than a password, but it is not renewable, and may be publicly available to anyone.
Multi-Factor Authentification 




In case of multi-factor authentication relying on proof of knowledge and proof of owning, the 2FA is often combined as:
- the password is directly input in the physical device, in order to unlock the embedded secret. The physical device is therefore accountable for the verification of the proof of knowledge.
- the password and the physical device both send independently their secret to the authentication server.
Note: MFA does not necessarily provide strong authentication. For example, a 2FA based on a password and an SMS is not secure.
There is something about passwords.
Passwords are the worst! 
Passwords are the most common type of authentication, however they are also poorly efficient for security.
- New password policies are published almost every year, and always come up with changing requirements: complexity, length, rotation, reuse, passphrase… We are compelled to remember hundreds of passwords, and efficient cloud-based password managers are very often not allowed.

- Passwords are also costly as they bully IT support teams with endless password resets.

- Furthermore, most of the attacks don’t even care about password complexity because they already have the full password available (black-market credential leakage exploiting reused passwords, phishing, keystroke logging, writing on a post note…
 ). Clipping levels already protect against basic password spraying attacks on authentication forms. Complexity only protects against bruteforce attacks against stolen hash files.
). Clipping levels already protect against basic password spraying attacks on authentication forms. Complexity only protects against bruteforce attacks against stolen hash files. 
In the end, passwords are not secure.
Note: Yet another punchline: Hackers don’t break in, they log in! Refer to this excellent article.
Hacking the MFA
Not all MFA are equal. And almost all of them are breakable. Let’s collate some efficient techniques!
- Phishing: Kindly ask for password, PIN… or politely ask to accept a push notification

- Phishing: Send fake URL imitating the authentication page
- Bruteforcing (Password, OTP…)

- Credential stuffing
- Shoulder surfing

- Use the password recovery procedure
- Replay attacks
- Interception (MitM on unauthenticated or plain text protocol, such as SMS, emails, HTTP…)
- MFA fatigue (MFA bombing, MFA spamming)
- SIM swap

- Abuse weak verification (false positives on fingerprints, use generative AI…)
- Compromised end-user device (spyware such as keylogger)
- Post authentication token stealing
- Capture victim physical attributes (record voice, collect fingerprint…)

- 3rd party access (rogue application with identity delegation)
- Physical attack (coercion, with force, weapon…)

Let’s go wild passwordless 
The purpose of passwordless is to eradicate the use of passwords. The process still uses MFA, but mostly relies on authentication and biometric factors. The FIDO2 specifications illustrate how the combination of a possession factor (such as a hardware Yubikey) and a biometric factor (fingerprint, face picture) drastically improve security.
Note: Let’s fight a common misconception! ![]() PINs, in the context of passwordless, are much more secure than passwords, because they never leave the endpoint device. Therefore, it reduces the risk associated with stolen credential files, or phishing emails.
PINs, in the context of passwordless, are much more secure than passwords, because they never leave the endpoint device. Therefore, it reduces the risk associated with stolen credential files, or phishing emails.
Examples of authentication schemes
Password-based authentication
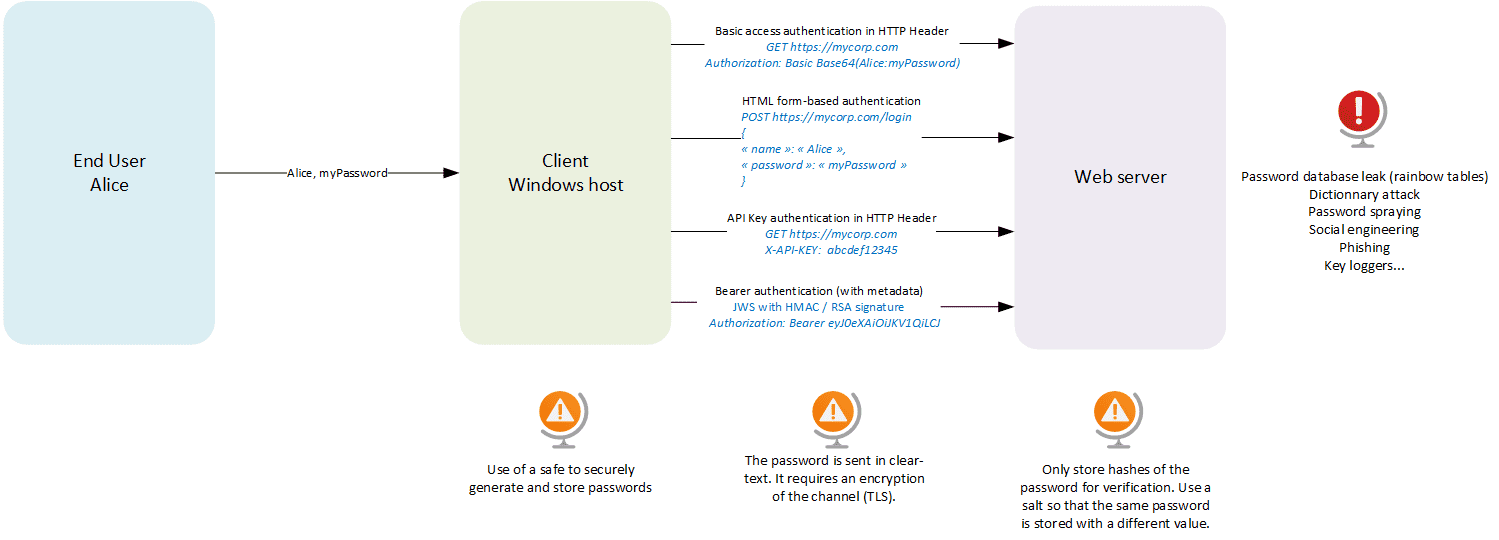
Let’s assume that Alice wants to authenticate with her very strong passphrase “password”! ![]()
Cryptographic authentication
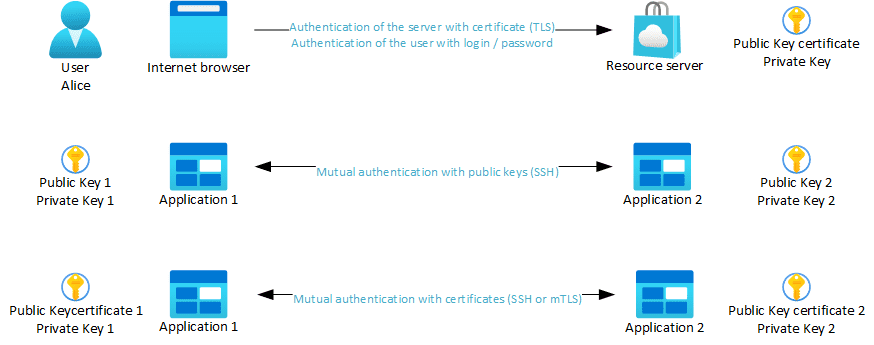
A session key is obtained with a combination of ECDHE 256 bits and ECDSA 256 bits. Then, this session key protects the session with AES 256 bits. ![]()
Note: It is not recommended to directly transmit a session key with RSA because it does not provide Perfect Forward Secrecy. If strictly required, RSA 2048 bits shall be used. Ephemeral Diffie-Hellman permits to obtain a shared secret over a public channel, with perfect forward secrecy property. But it is vulnerable to man in the middle, so it is used in combination with ECDSA for authentication.
Note: Based on original learning material from ANSSI documentation Recommendations relatives à l’authentification multifacteur et aux mots de passe, and from Microsoft report Passwordless protection: Reduce your risk exposure with passwordless authentication.