DoT, DoH and DNSSEC
DoT and DoH
The DNS protocol used for domain name resolution is natively insecure. ![]() It is built upon UDP datagrams sent on port 53 of DNS servers. Therefore, it does not authenticate the destination server, and all the data is sent in clear text.
It is built upon UDP datagrams sent on port 53 of DNS servers. Therefore, it does not authenticate the destination server, and all the data is sent in clear text.
Just use your favourite packet sniffer to capture the DNS resolution, and seriously impact our web browsing privacy! Have a look at this plain text DNS query for the kartapuce.com domain. ![]()
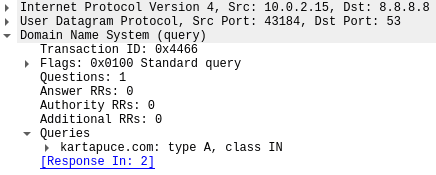
Hopefully, our good TLS friend can help us! With DNS over TLS (DoT), DNS traffic is wrapped within the TLS protocol, and TCP packets are sent fully encrypted over port 853. As another option, the DNS over HTTPS (DoH) protocol encapsulates DNS traffic within the HTTPS protocol over port 443. With these two options, the destination DNS server is authenticated, and DNS queries and answers are fully encrypted. ![]()
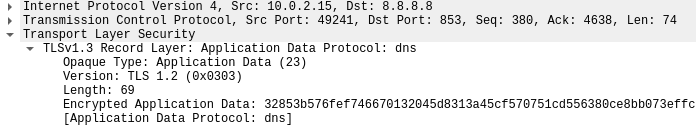
Let’s start by a capture of DoT queries to kartapuce.com.
We can now compare it with DoH queries!
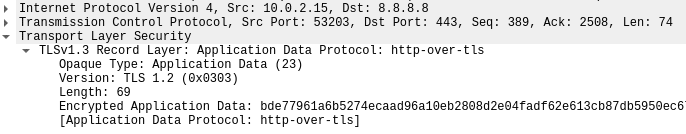
DoT has less latency than DoH, and is much easier to filter for our beloved network administrators. ![]() However, DoH provides even more privacy since DNS queries are hidden within the huge HTTPS traffic.
However, DoH provides even more privacy since DNS queries are hidden within the huge HTTPS traffic.
DNSSEC
DoT and DoH achieve DNS server authentication. However, due to the recursive approach of DNS and to the numerous DNS caching servers, the DNS records are often not directly provided by the authoritative DNS servers. It would be fantastic to be able to directly authenticate the DNS records! It is possible with Domain Name System Security Extensions (DNSSEC). ![]() DNSSEC is still not largely adopted. It is a complex process that requires extensive knowledge for its initial setup and ongoing configuration. It is recommended to perform a risk analysis before rushing headlong into DNSSEC.
DNSSEC is still not largely adopted. It is a complex process that requires extensive knowledge for its initial setup and ongoing configuration. It is recommended to perform a risk analysis before rushing headlong into DNSSEC. ![]()
DNSSEC provides protection against DNS cache poisoning. ![]() However, if an attacker has breached a DNS domain and is able to sign a DNS record, that is yet another issue!
However, if an attacker has breached a DNS domain and is able to sign a DNS record, that is yet another issue!
Let’s establish a chain of trust with DNSSEC!
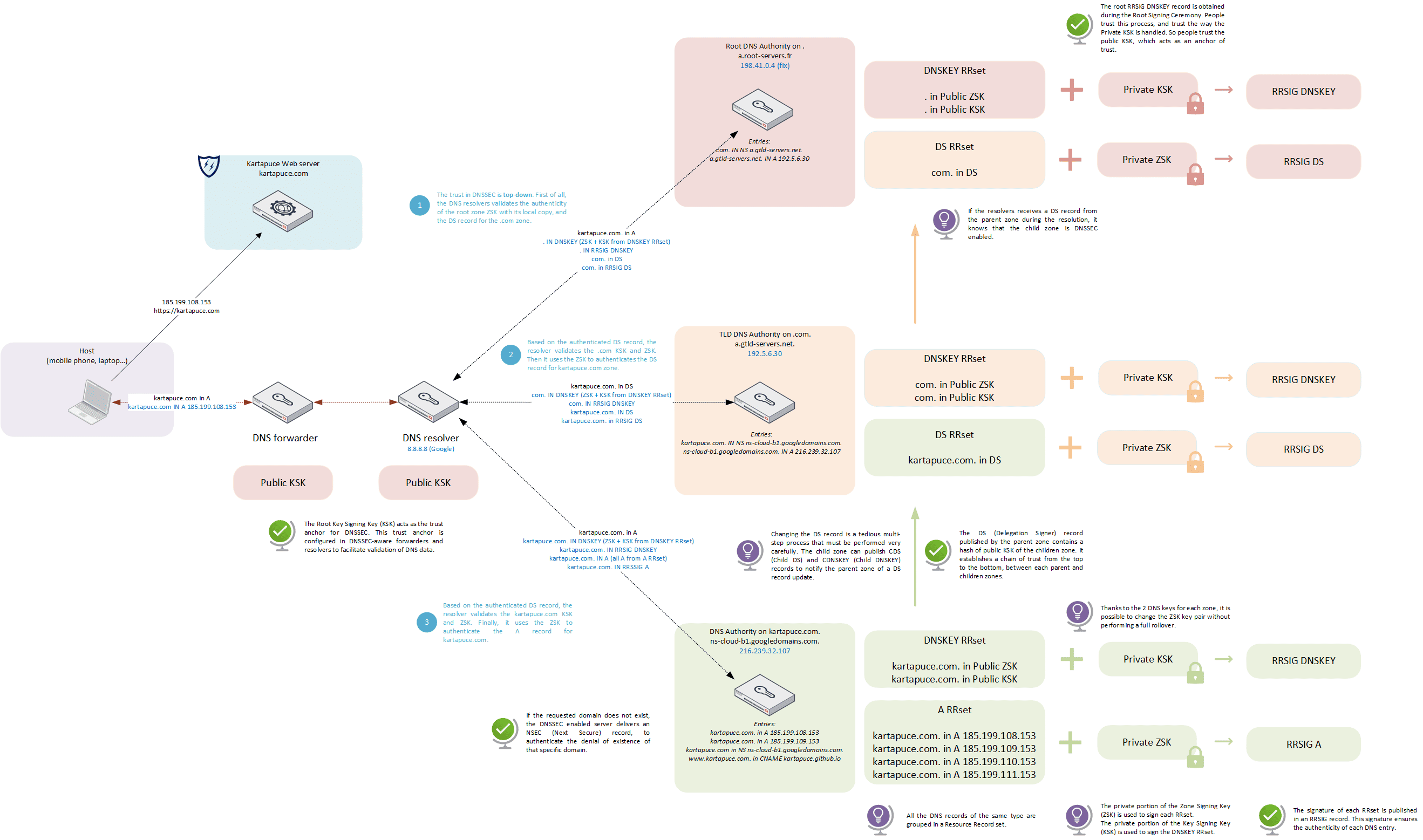
Watch out cyber nerds, the Root Signing Ceremony is about to begin. What’s going to happen today: new ZSK, new hardware? ![]()
Note: The dig and devl commands will be your most valuable friends to understand the fabulous world of DNS queries. Have a look at the following commands!
- dig @8.8.8.8 domain +dnssec
- delv @8.8.8.8 domain +dnssec +vtrace
Note: Based on original learning from Cloudflare engineers.